2024.06.19.보안 day52
보안뉴스 : https://knvd.krcert.or.kr/domesticVul.do
SNORT (IDS)
[ vi /etc/snort/local ] / snort -i ens33 -c local / tail -f /var/log/snort/alert / vi /etc/sysconfig/iptables
alert은 10.10.10.100 에서 hping3 는 칼리20.20.20.20에서 실습
request와 reply
alert icmp 20.20.20.20 any -> 10.10.10.10 any (msg:"REQUEST_ICMP"; itype:8; sid:50007;)
alert icmp 10.10.10.10 any -> 20.20.20.20 any (msg:"REPLY_ICMP"; itype:0; sid:50008;)
threshold : 5개마다 탐지 / 10초동안 5번이상의 패킷에 대해서 5개마다 1번 탐지
alert icmp any any -> 10.10.10.10 any (msg:"THRESHOLD";threshold:type threshold,track by_src,count 5,seconds 10; sid:50009;)
limit : 5까지 탐지 / 10초동안 5번이상의 패킷에 대해서 5개만 탐지
alert icmp any any -> 10.10.10.10 any (msg:"LIMIT"; threshold:type limit,track by_src,count 5,seconds 10; sid:50010;)
both : 1개만 탐지 / 10초동안 50번이상의 패킷에 대해서 1개만탐지
alert icmp any any -> 10.10.10.10 any (msg:"BOTH"; threshold:type both,track by_src,count 50,seconds 10; sid:50011;)
hping3 --icmp 10.10.10.10 --flood
ping of death : 단편화가 되고 파일이 일정시간 이상 들어올때 차단
hping3 --icmp -d 40000 10.10.10.10 --flood
= hping3 -1 -d 40000 10.10.10.10 --flood
alert ip any any -> 10.10.10.10 any (msg:"PING_OF_DEATH";threshold:type both,track by_src,count 50, seconds 10; fragbits:M;sid:50012;)
Land attack : 출발지와 도착지 IP가 같은 경우 탐지
hping3 --icmp -a 10.10.10.10 10.10.10.10 --flood
alert icmp any any -> 10.10.10.10 any (sid:50013; msg:"Lend Attack"; sameip; threshold:type both, track by_src, count 20, seconds 10;)
smuf_attack : ip속여 피해자의 브로드캐스트로 ping , 속인 ip가 반격 받음
alert icmp any any -> 255.255.255.255 any (msg:"Smuf attack";itype:8; threshold:type both,track by_dst,count 20,seconds 10; sid:50014;)
hping3 -1 -a 30.30.30.30 10.10.10.255 --flood
TCP_SYN_FLOODING
alert tcp any any -> 10.10.10.10 80 (\
sid:50015; msg:"TCP_SYN_FLOODING"; flags:S; threshold:type both,track by_dst,count 20,seconds 10;)
hping3 --rand-source 10.10.10.10 -p 80 -S --flood
- S : SYN 패킷
TCP__Connect_FOODING
alert tcp any any -> 10.10.10.10 80 (\
sid:50016; msg:"TCP_Connect_FLOODING"; flags:A; threshold:type both,track by_dst,count 20,seconds 10;)
nping --tcp-connect -p 80 -rate=90000 -c 90000 -q 10.10.10.10
** tcp_syn _flooding 과 tcp_connect_flooding은 ack이 나오냐 안나오냐로 구분한다
tcp_syn_flooding만 정확하게 구분할수없다
UDP_FOODING
alert udp !10.10.10.100 any -> 10.10.10.10 any (sid:50017; msg:"UDP_FLOODING"; threshold:type both,track by_src,count 20,seconds 10;)
hping3 -2 10.10.10.10 --flood
X-MAS
alert tcp !10.10.10.10 any -> 10.10.10.10 any (msg:"X-MAS SCAN -sX";\
flags:UPF; threshold:type both,track by_src,count 20,seconds 10; sid:50020;)
hping3 -tcp 10.10.10.10 --flood
**urg, psh,fin
FIN SCAN
alert tcp !10.10.10.10 any -> 10.10.10.10 any (msg:"FIN SCAN -sF";\
flags:F; threshold:type both,track by_src,count 20,seconds 10; sid:50021;)
SYN SCAN
alert tcp !10.10.10.10 any -> 10.10.10.10 any (msg:"SYN SCAN -sS";\
flags:S; threshold:type both,track by_src,count 20,seconds 10; sid:50022;)
NULL SCAN
alert tcp !10.10.10.10 any -> 10.10.10.10 any (msg:"NULL SCAN -sN";\
flags:0; threshold:type both,track by_src,count 20,seconds 10; sid:50023;)
** 웹은 대부분 시그니처 공격으로 되기때문에 pcre (패턴) , content (문자열)를 사용해서 필터링을 함
웹사이트 SNS 접속확인
alert tcp 10.10.10.10 any -> any 443 (msg:"SNS_ACCESS";pcre:"/facebook.com|instagram.com/"; sid:50040;)
SQL_injection 확인 : 게시판 board_view.php 기준
alert tcp any any -> 10.10.10.10 80 (msg:"sql_injection";pcre:"/UNION|SELECT|OR|%27|%23/i";content:"board_view.php"; sid:50041;)
xxs 확인
alert tcp any any -> 10.10.10.10 80 (msg:"xss_attack";content:"script";nocase; sid:50042;)
ssh 에 hydra 로 brute force 공격을 탐지하는 정책
alert tcp any any -> 10.10.10.10 22
(sid:50050; msg:"SSH_Brute Force";threshold:type both,track by_dst,count 10,seconds 10; flags:S;)
**SSH 접속 시 초기에는 SYN 패킷이 사용되므로 flags 는 S
hydra -l sevas -x 1:1:1a! ftp://192.168.1.10 -V
10.10.10.10)
yum groupinstall "Development Tools"
yum groupinstall "GNOME Desktop" "Graphical Administration Tools"
yum install cifs-utils
https://tomcat.apache.org/download-90.cgi
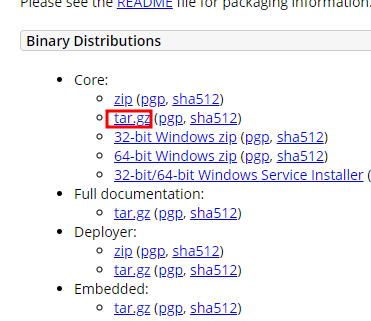
https://www.oracle.com/java/technologies/javase/jdk15-archive-downloads.html
301 ㅗㅑㄴ
301 ll
302 yum install cifs-utils
303 mkdir /mount
304 mount -t cifs //10.10.10.1/0_share /mount
cp -a /mount/apache-tomcat-9.0.89.tar.gz ./
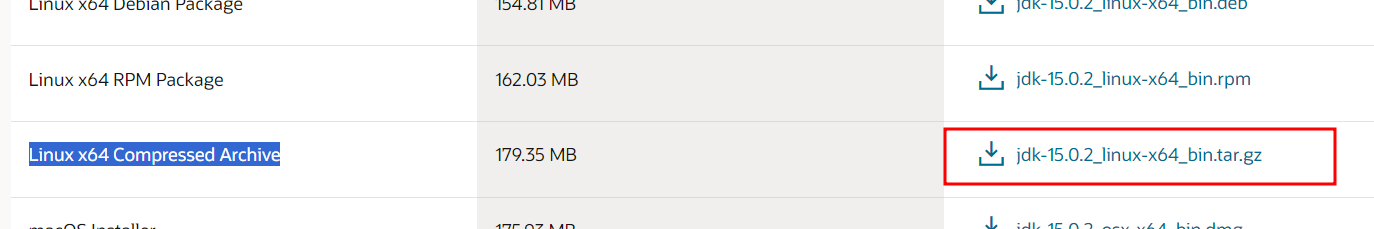
374 cp -a /mount/jdk-15.0.2_linux-x64_bin.tar.gz ./
316 ll
317 tar xvf apache-tomcat-9.0.89-fulldocs.tar.gz
318 tar xvf jdk-15.0.2_linux-x64_bin.tar.gz
[root@www local]# echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/root/bin
링크 만들기
381 ln -s src/apache-tomcat-9.0.89 tomcat
382 ln -s src/jdk-15.0.2 java
384 mkdir -p /backup/java
385 cp -a java/ tomcat/ /backup/java/
386 vi /etc/profile
TOMCAT=/usr/local/tomcat
JAVA_HOME=/usr/local/java
PATH=$PATH:$JAVA_HOME/bin:$TOMCAT/bin
CLASSPATH=$TOMCAT/lib/servlet-api.jar:$TOMCAT/lib/jsp-api.jar
export JAVA_HOME PATH CLASSPATH
387 source /etc/profile
388 java --version
389 javac --version
390 /usr/local/tomcat/bin/startup.sh start
391 netstat -lntup |grep 8080
cd /usr/local/tomcat/webapps/ROOT
vi hello.jsp
<%@ page contentType="text/html; charset=euc-kr" %>
<%! String str = "Hello World! JSP!"; %>
<html>
<head>
<title>::: <%=str%> :::</title>
</head>
<body>
<center>
<h1> Hello JSP </h1>
<P>
<% out.println(str); %>
</center>
</body>
</html>
13.톰캣 끄기
/usr/local/tomcat/bin/shutdown.sh
다 내리고
192.168.10.10 록키 새로시작 )
service NetworkManager restart
nmcli con up "System ens33" <====== 이거 안해서 ping8.8.8.8 오류남
*순서 주의 *
dnf groupinstall "Development Tools"
dnf install -y bc binutils compat-openssl10 elfutils-libelf glibc glibc-devel ksh libaio libXrender libX11 libXau unixODBCdnf install -y libnsl sysstat
dnf install -y libXi libgcc libnsl libXtst libstdc++ libxcb libibverbs make policycoreutils policycoreutils-python-utils smartmontools sysstat
cd /usr/local/src
wget https://yum.oracle.com/repo/OracleLinux/OL8/appstream/x86_64/getPackage/oracle-database-preinstall-21c-1.0-1.el8.x86_64.rpm
dnf install oracle-database-preinstall-21c-1.0-1.el8.x86_64.rpm
wget https://download.oracle.com/otn-pub/otn_software/db-express/oracle-database-xe-21c-1.0-1.ol8.x86_64.rpm
dnf install epel-release
dnf install rlwrap
57 blkid
58 vi /etc/fstab
59 mkdir /opt
60 mount -a
61 vi /etc/fstab
62 mount -a
63 df -h
64 dnf install oracle-database-xe-21c-1.0-1.ol8.x86_64.rpm
65 /etc/init.d/oracle-xe-21c configure
cat /opt/oracle/homes/OraDBHome21cXE/network/admin/listener.ora
vi /opt/oracle/homes/OraDBHome21cXE/network/admin/listener.ora
passwd oracle
vi .bashrc
alias sqlplus='rlwrap sqlplus'
vi /home/oracle/.bash_profile
export ORACLE_BASE=/opt/oracle
export ORACLE_HOME=/opt/oracle/product/21c/dbhomeXE
export ORACLE_SID=XE
export PATH=$PATH:$ORACLE_HOME/bin
export LD_LIBRARY_PATH=$ORACLE_HOME/lib:/lib:/usr/lib:/usr/local/lib
export TNS_ADMIN=$ORACLE_HOME/network/admin
export CV_ASSUME_DISTID=OEL8.4
export NLS_LANG=KOREAN_KOREA.AL32UTF8
systemctl enable oracle-xe-21c
init 6
oracle계정접속
su - oracle
set |grep -i oracle
sqlplus / as sysdba
create user c##demo identified by 1234 default tablespace users quota unlimited on users;
grant resource,connect to c##demo;
connect c##demo
카톡에서 받은 코드로
DB 채우기
98 dnf install java-17-openjdk java-17-openjdk-devel
99 alternatives --config java
100 java --version
101 javac --version
102 dnf install autoconf libtool httpd-devel
103 cd /usr/local/src/
105 ll
106 wget https://dlcdn.apache.org/tomcat/tomcat-9/v9.0.89/bin/apache-tomcat-9.0.89.tar.gz
107 ll
108 useradd -r -d /opt/tomcat -s /bin/false -c "Tomcat User" tomcat
111 cd /opt/
112 ll
113 cp -r /etc/skel/ tomcat
114 ll
115 chown -R tomcat. tomcat
116 ll
117 tar xvf /usr/local/src/apache-tomcat-9.0.89.tar.gz -C /opt/tomcat --strip-components=1
118 cd tomcat/
119 ll
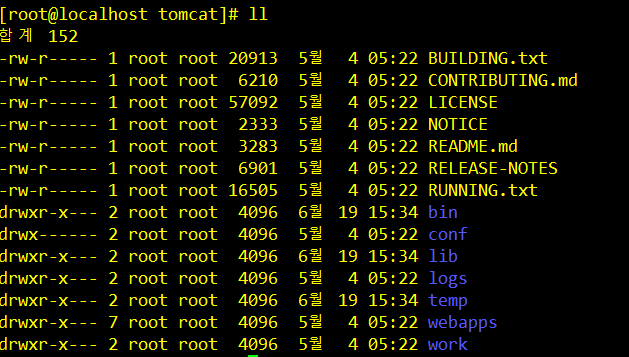
[root@localhost tomcat]# vi /opt/tomcat/conf/tomcat-users.xml
<role rolename="manager-gui"/>
<user username="admin" password="1234" roles="manager-gui,admin-gui"/>
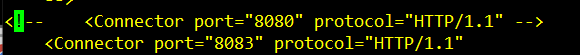
[root@localhost tomcat]# vi conf/server.xml
69 <!-- <Connector port="8080" protocol="HTTP/1.1" -->
70 <Connector port="8083" protocol="HTTP/1.1"
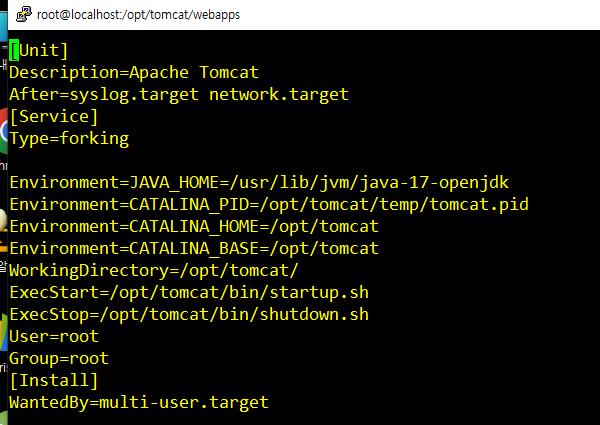
vi /etc/systemd/system/tomcat.service
[Unit]
Description=Apache Tomcat
After=syslog.target network.target
[Service]
Type=forking
Environment=JAVA_HOME=/usr/lib/jvm/java-17-openjdk
Environment=CATALINA_PID=/opt/tomcat/temp/tomcat.pid
Environment=CATALINA_HOME=/opt/tomcat
Environment=CATALINA_BASE=/opt/tomcat
WorkingDirectory=/opt/tomcat/
ExecStart=/opt/tomcat/bin/startup.sh
ExecStop=/opt/tomcat/bin/shutdown.sh
User=root
Group=root
[Install]
WantedBy=multi-user.target
http://192.168.10.10:8083/DemoProjV2/ 안열리는 오류
147 vi /opt/tomcat/conf/tomcat-users.xml
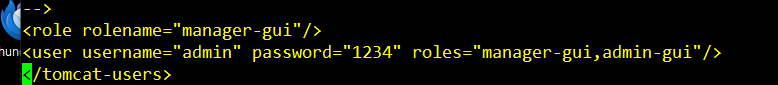
153 vi /opt/tomcat/conf/server.xml
154 vi /etc/systemd/system/tomcat.service
149 service tomcat.service
150 service tomcat start
151 systemctl status tomcat
155 systemctl daemon-reload
156 systemctl start tomcat
157 systemctl enable tomcat
198 198 service oracle-xe-21c stop
199 service oracle-xe-21c start
netstat -lntup 에서 8083 열렸는지 확인
239 service firewalld stop => 방화벽 안열어서 그럼
240 systemctl disable firewalld
192.168.10.10:8083/DemoProjV2
192.168.10.10:8083/DemoProjV2
yejin
asdqwe123!@#
기밀성-암호화
보안장비 => NAC / ACL
시스템 보안 ==> 악성코드 공격 . rootkit? / password 계정 권한 => 해시코드 트리바이어? / setuid점검 /
웹보안 = > owsap / ids ips / 웹쉘 원격접속
네트워크 보안 - 스니핑 스푸핑
무결성-
이것들이 다 있는게 UTM
이제 UTM 장비에 대해 배운다
소포스
https://www.sophos.com/en-us/support/downloads/utm-downloads
Cybersecurity as a Service Delivered | Sophos
We Deliver Superior Cybersecurity Outcomes for Real-World Organizations Worldwide with a Broad Portfolio of Advanced Security Products and Services.
www.sophos.com
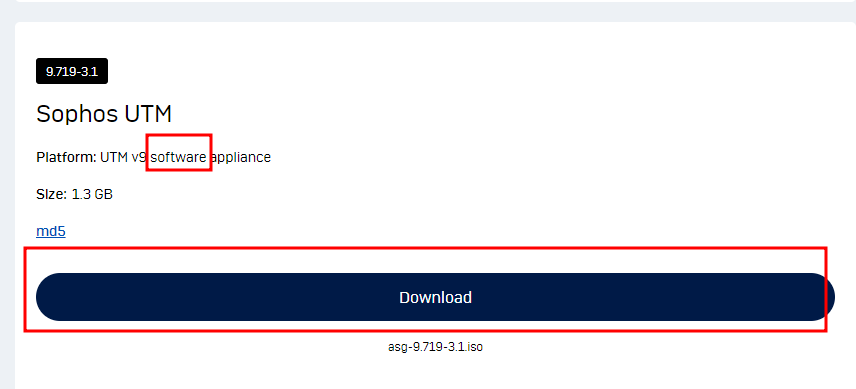
sophos software 다운로드
https://192.168.10.100:4444/
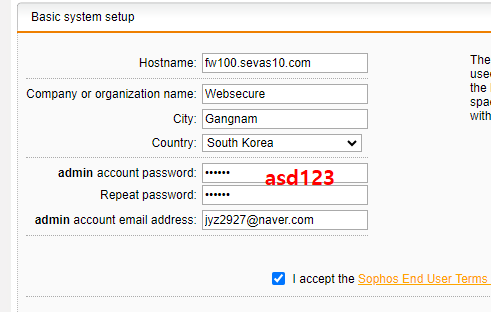
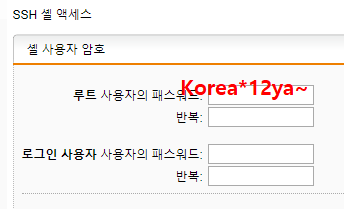
비번 asd123 말고 Korea*12ya~ 이거로 바꿈
로그인
admin
Korea*12ya~
DMZ_SERVER mini 10.10.10.10
UTM 192.168.10.100
칼리 20.20.20.20